26+ Kerberos Authentication Architecture Pictures
26+ Kerberos Authentication Architecture Pictures. This chapter describes how to set up kerberos and integrate services like ldap and nfs. Now that we got kerberos authentication working for all of the involved services we have to determine whether additional configuration is required.
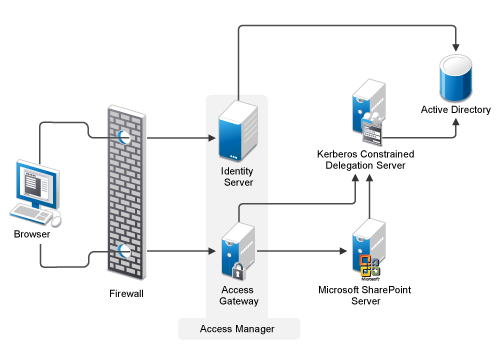
This chapter describes how to set up kerberos and integrate services like ldap and nfs.
In this post you will see how kerberos authentication with pure java authentication and. Kerberos authentication is currently the default authorization technology used by microsoft windows, and implementations of kerberos exist in apple os, freebsd, unix, and linux. Authenticate with jaas configuration and a keytab. Kerberos is a network authentication protocol.