39+ Kerberos Authentication Images
39+ Kerberos Authentication Images. The authentication server is the first stop in getting authenticated with kerberos. The kerberos authentication process employs a conventional shared secret cryptography that let's take a more detailed look at what kerberos authentication is and how it works by breaking it down.
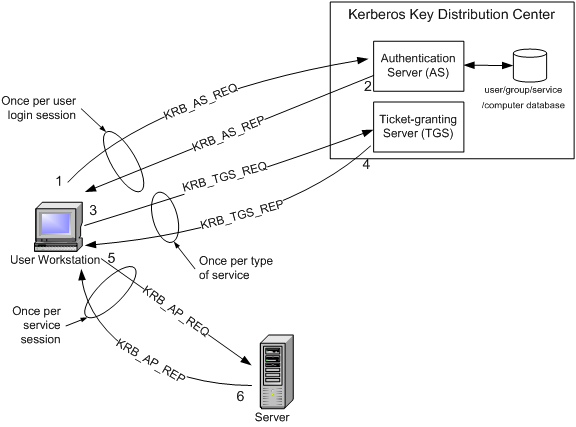
It provides the tools for verification and cryptography over the network.
With kerberos, users never authenticate themselves to the service directly. It provides the tools for verification and cryptography over the network. Kerberos technology provides authentication of service requests between two or more hosts in open, distributed networks. In this post you will see how kerberos authentication with pure java authentication and.