28+ Authentication Process Of The Kerberos Environment Images
28+ Authentication Process Of The Kerberos Environment Images. Kerberos helps you meet these requirements by providing strongly encrypted authentication. Let us say a user wishes to access a network file server to read a document.
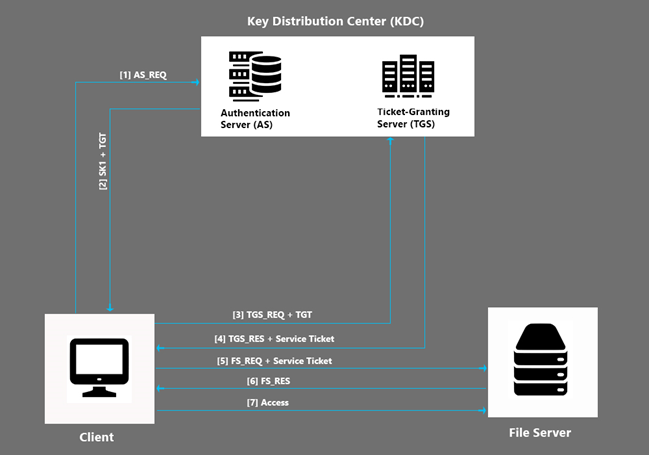
Kerberos has three parties taking actions in the authentication process.
Some screenshots to aid in the process: Remember how the client no longer first and foremost is the need of the kerberos server. This paper gives an overview of the kerberos authentication model as implemented for mit's project athena. In computer, kerberos is an authentication protocol based on the exchange of tickets.